Received July 2014
From:
Date: Wed, Jul 2, 2014 at 12:42 PM
Subject: RE: Webmail Verification
To:
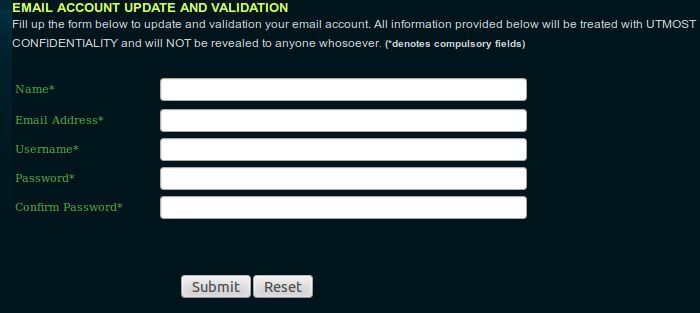
*Dear mailbox user,*
*Your Email Account have been violated, unsuspicious activities was
noticed in your email account and your account will be disabled shortly.*
*you are required to verify your email account to prevent your email
account from being disabled. click on our ITS-SUPPORT
<http://xxxxxxxxx.tripod.com/>*
<http://xxxxxxxxx.tripod.com/>*to fill out the necessary
information to secure and verify your account*
*Additional Info Staff,Student and Faculty Members Only.* *Click on
Staff and Faculty ACCESS-PAGE <http://xxxxxxxxxx.tripod.com/>*
*IMPORTANT NOTE**:* *Your account will be disabled if not verified within
the next 24hours**.*
*ITS help desk **ADMIN TEAM*
*�Copyright 2014 Microsoft*
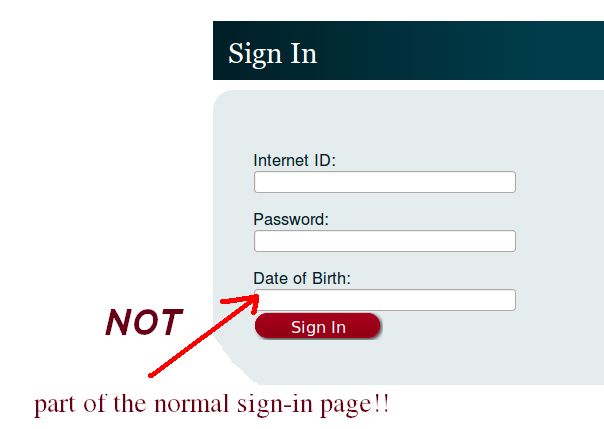
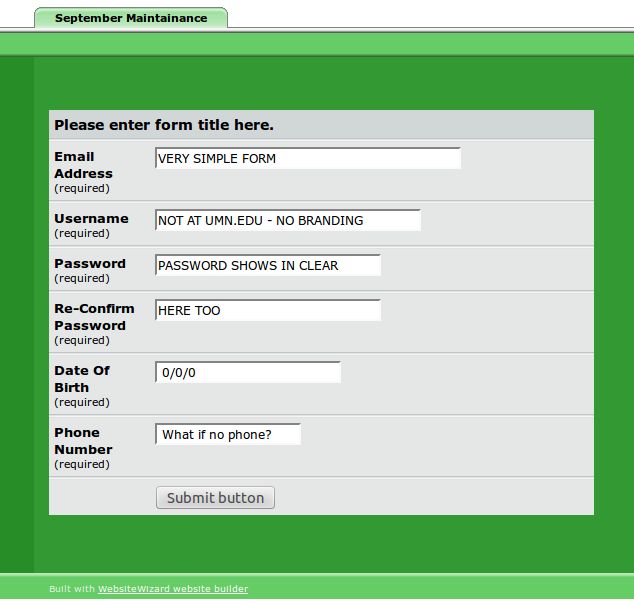
Nope, no UMN branding, advertisements... AND hosted at tripod.com?